| In need of multiple accounts? Our multi-account solution is designed for organizations seeking unique accounts for their various locations, departments, or users. Take advantage of bulk pricing, product features for brand control, customized onboarding, and more! |
Single sign-on (SSO) makes logging into your third-party platforms, like Constant Contact, easier because you're able to authenticate your login credentials through a central domain, reducing the number of usernames and passwords needed to perform daily tasks. Partners who use SSO can enable their Constant Contact account to use existing user credentials to log into sub-accounts.
Constant Contact uses OpenID Connect (OIDC) as an identity authentication protocol to authenticate and authorize users for SSO. OIDC is built on top of the OAuth 2.0 framework and uses Web Tokens (JWT) to transfer data between two parties. Here is the basic flow:
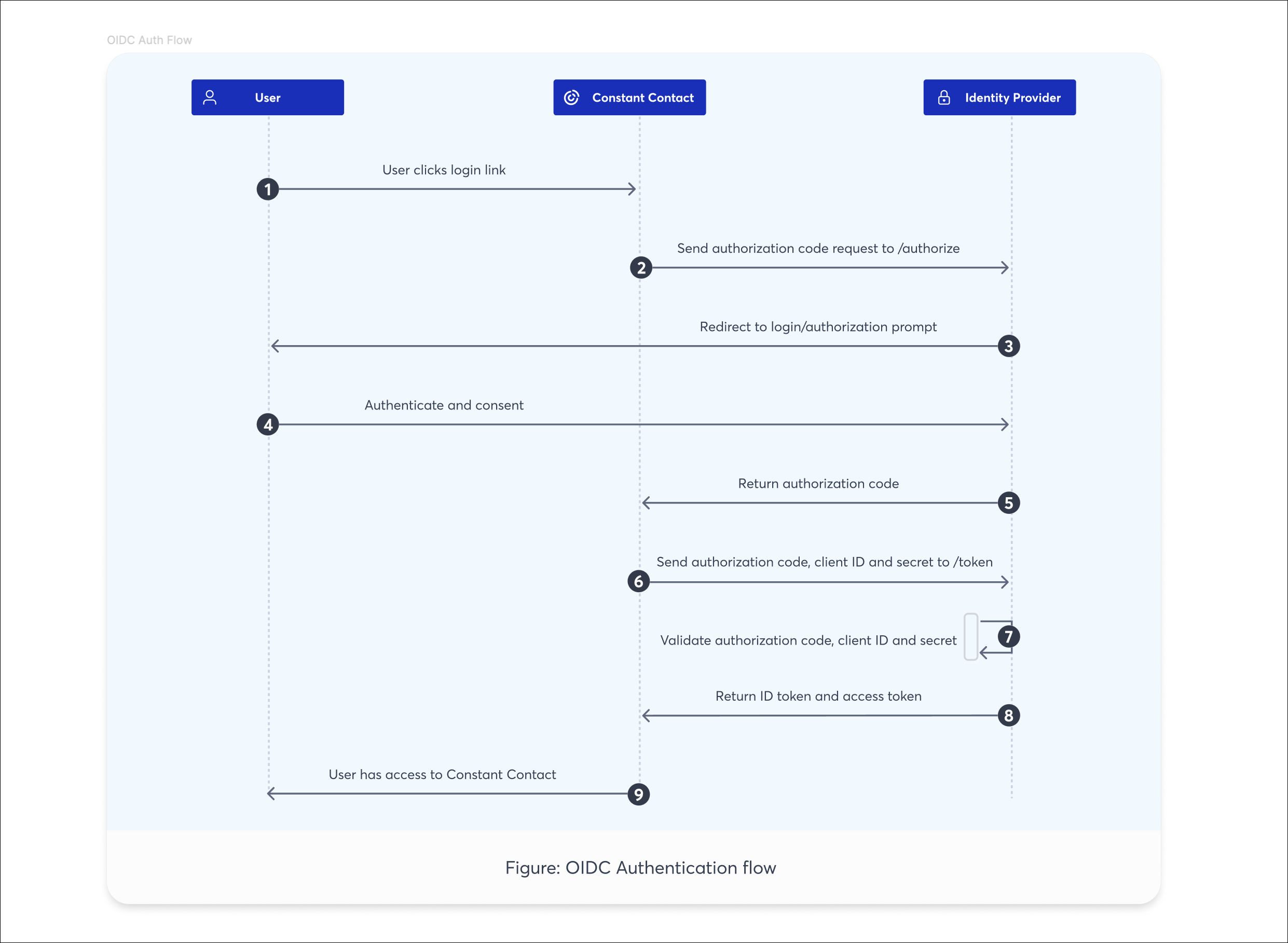
For more information on how OIDC works, please see the OpenID developers site.
Each Identity Provider (IdP) that supports OIDC has a Discovery URL where their various OIDC URLs are stored and can be retrieved by an application for enabling SSO. When setting up SSO through Constant Contact, you need:
Here is a list of the most common IdPs and their Discovery URLs. If you don't see your IdP listed, please contact them to obtain the Discovery URL. The Discovery URL is often customized with your unique domain.
| Identity Provider | OIDC Discovery URL |
| Amazon Cognito | https://cognito-idp.{region}.amazonaws.com/{userPoolId}/.well-known/openid-configuration |
| Apple ID | https://appleid.apple.com/.well-known/openid-configuration |
| Auth0 | https://{yourDomain}/.well-known/openid-configuration |
| Cisco Duo | https://sso-abc1def2.sso.duosecurity.com/oauth/DIABC123678901234567/.well-known/oauth |
| Facebook Login | No Discovery URL — custom flow with OIDC-like behavior |
| Frontegg | https://[your-frontegg-subdomain].frontegg.com/.well-known/openid-configuration |
| Google Workspace | https://accounts.google.com/.well-known/openid-configuration |
| JumpCloud | https://oauth.id.jumpcloud.com/.well-known/openid-configuration |
| Keycloak | https://{host}/auth/realms/{realm}/.well-known/openid-configuration |
| LoginRadius | https://cloud-api.loginradius.com/sso/oidc/v2/{sitename}/{oidcappname}/.well-known/openid-configuration |
| Microsoft Entra (formerly Azure Active Directory) | https://login.microsoftonline.com/{tenant-id}/v2.0/.well-known/openid-configuration |
| Okta | https://{yourOktaDomain}/.well-known/openid-configuration |
| OneLogin | https://{yourDomain}.onelogin.com/oidc/2/.well-known/openid-configuration |
| Ping Identity | https://{env-id}.pingidentity.com/as/.well-known/openid-configuration |
| SecureAuth | https://.../secureauth1/.well-known/openid-configuration |
| WorkOS | https://.authkit.app/.well-known/openid-configuration |
An Identity Provider (IdP), like Auth0, Cisco Duo, Microsoft Entra, Okta, PingOne, etc., is needed in order to enable SSO.
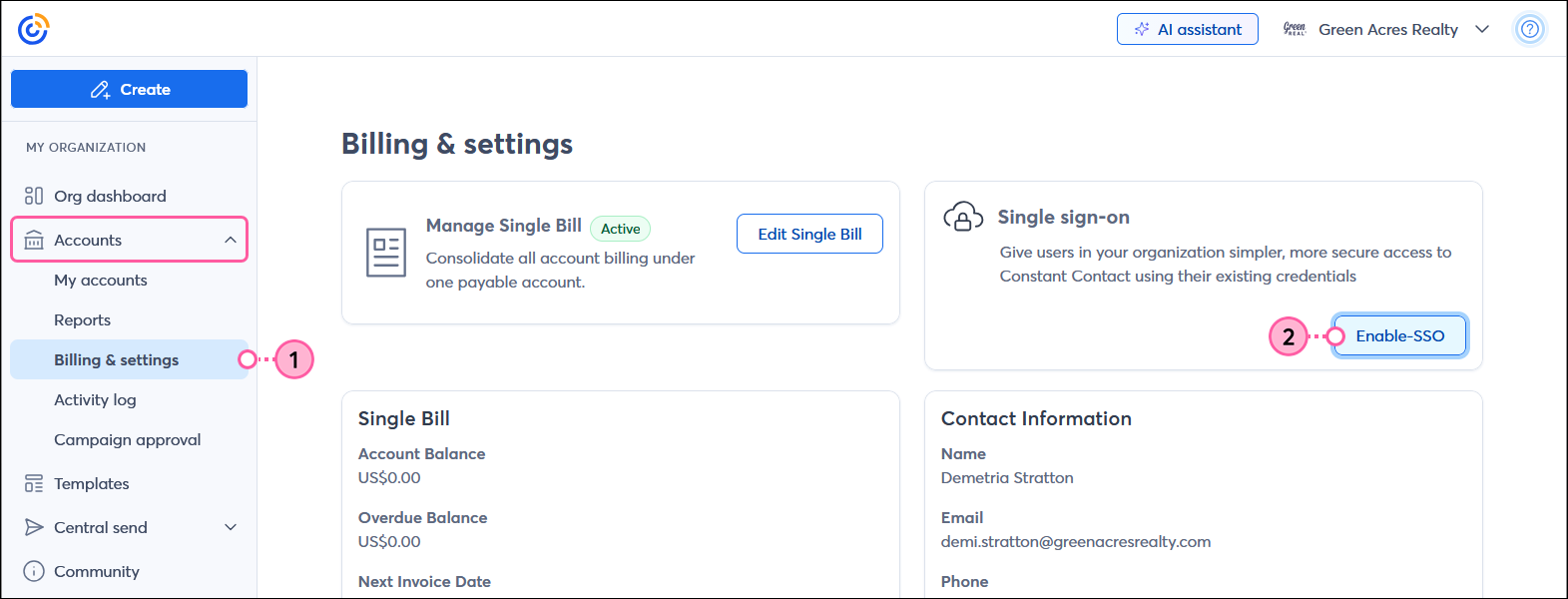
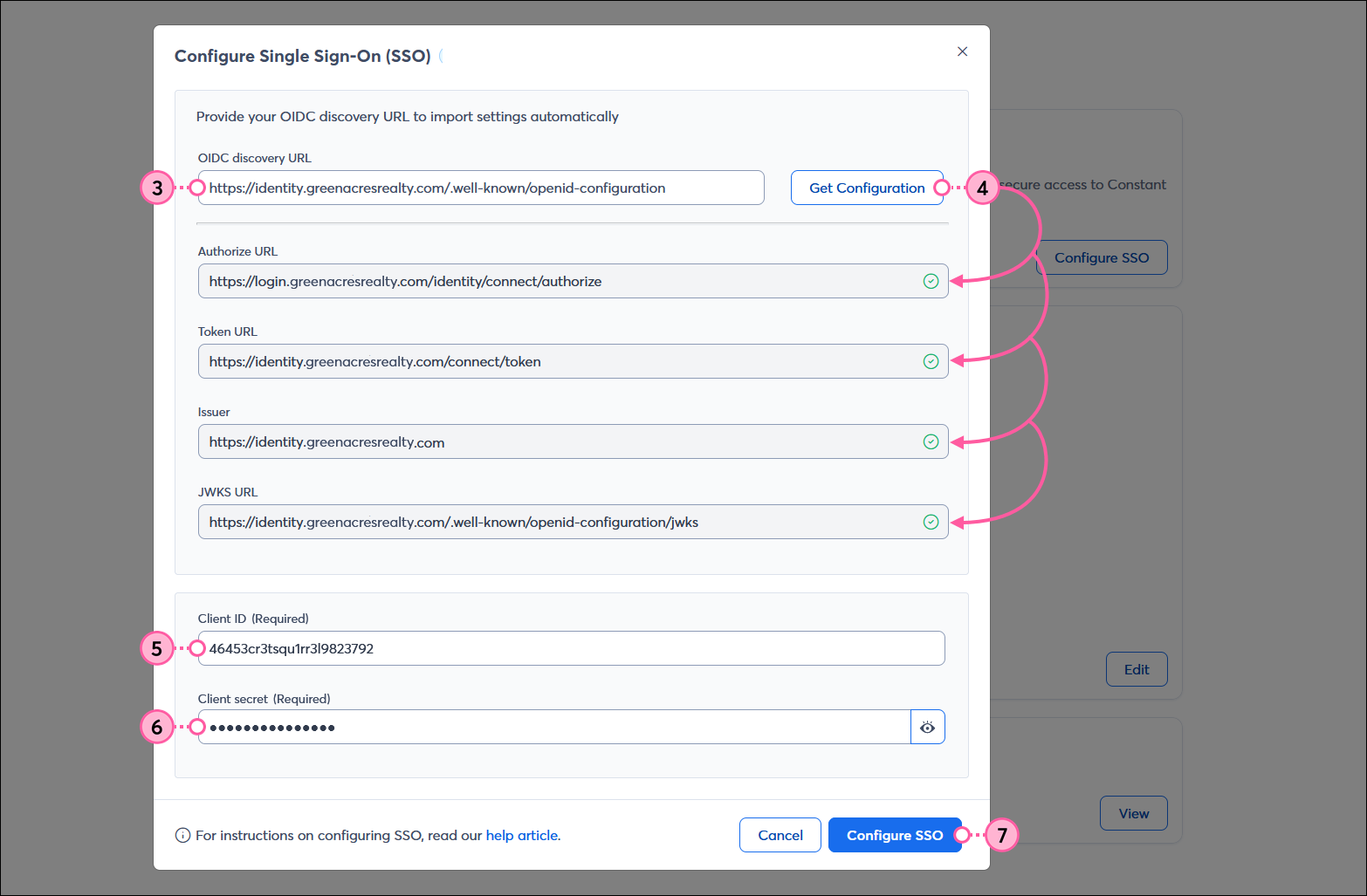
Once SSO is enabled for your Constant Contact account, you're able to edit your credentials if you switch to a different IdP, or disable SSO if you want to stop using it. SSO can always be re-enabled later. In addition, if you need a redirect URL to add to your IdP, or need to copy your Login URL or IdP name, you can do that too.

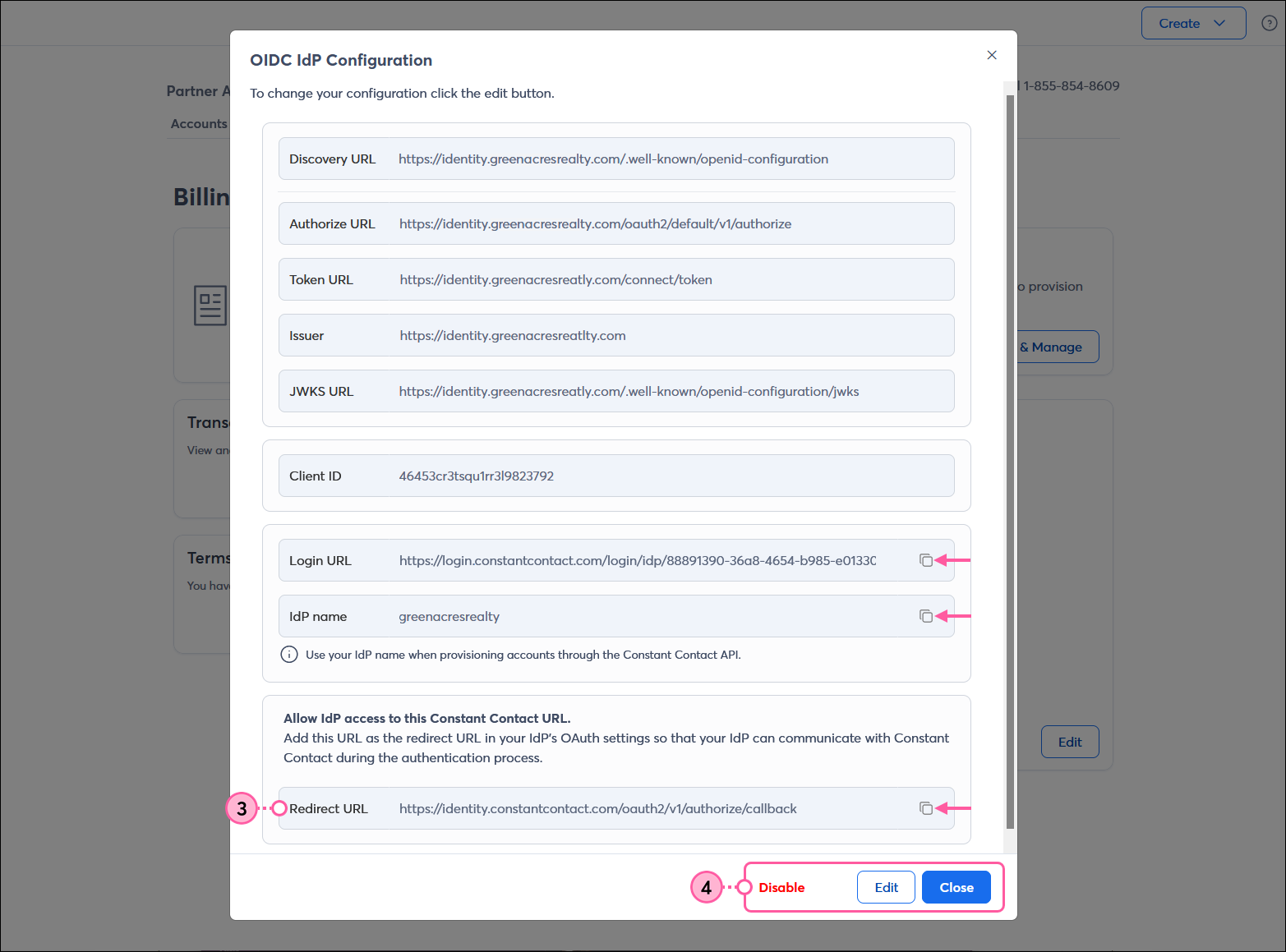
Any links we provide from non-Constant Contact sites or information about non-Constant Contact products or services are provided as a courtesy and should not be construed as an endorsement by Constant Contact.
Copyright © 2026 · All Rights Reserved · Constant Contact · Privacy Center